Sensitive data refers to data that needs protection from unauthorized disclosure. It’s important to safeguard access to sensitive research data, and any sharing of it should be carefully planned.
Examples of Sensitive Data
The OpenAIRE gives a few examples of sensitive data, which include:
- Personal identification data: identifiers such as names or identification numbers, health information, legal, economic, social characteristics, it also includes location data from GPS or mobile phones.
- Confidential data: trade secrets, investigations, data protected by intellectual property right, financial information, government classified information.
- Combination of different datasets that can be combined into identifiable data
- Biological data: endangered (plant or animal) species, where their survival is dependent on the protection of their location data (biodiversity community)
Prepare sensitive data for sharing
There are various ways to reduce the risk of individuals being identifiable. Even when you are sharing or presenting aggregated or summarized data, you still need to obtain permission, prepare your dataset, and consider proper access control.
Anonymization
Anonymization irreversibly removes any way of identifying the data subject by removing personal identifiers. It will prevent future re-identification, even by the original researchers.
Pseudonymization
Pseudonymization substitutes the identity of the data subject with other values. However, pseudonymized data is still considered sensitive because it can be linked back to a person, but it is a secure approach since personal identifiers are stored elsewhere.
Encryption
Encryption involves using strong encryption and proper key management to make sensitive data unintelligible to unauthorized access, reducing its re-usability. The HKUST ITSC Department provides several services to help protect your data via encryption.
Flowchart for Planning Sensitive Data Sharing
The flowchart shown below is designed by ARDC (Australian Research Data Commons), and it is a useful guide to help you determine when and how to publish sensitive data as openly and ethically as possible. You can use these questions to guide you through a good data sharing strategy.
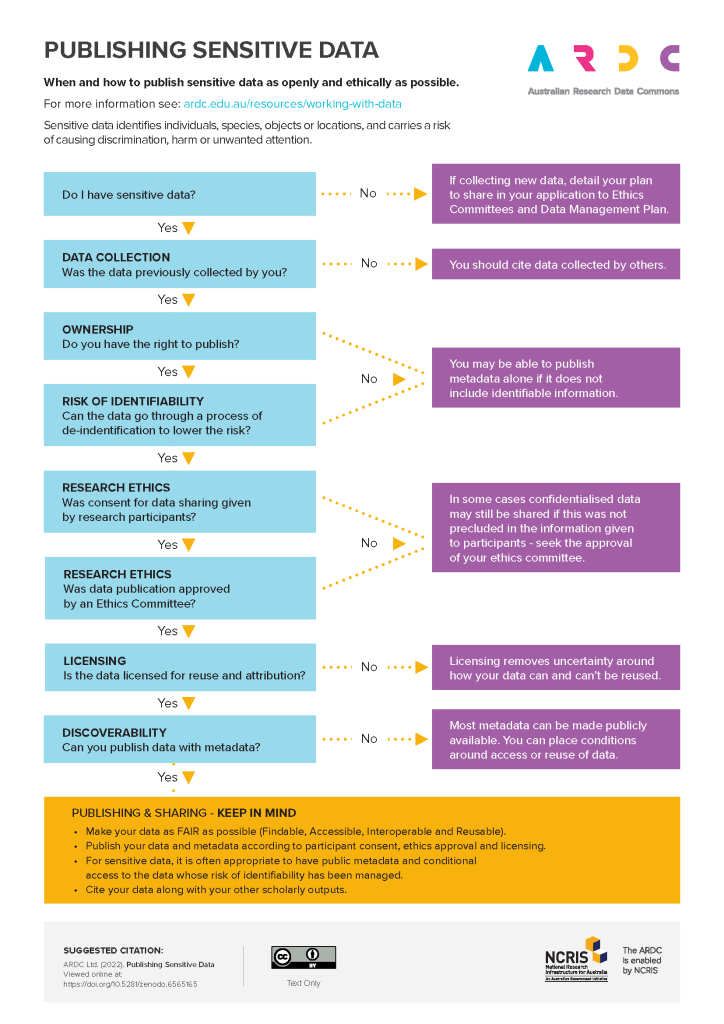
Eight questions that will help you work out when and how to publish sensitive data as openly and ethically as possible.
Keep in mind that even sensitive data can still meet the requirements of the FAIR Data Principles. It is often appropriate to have public metadata and conditional access to the data whose risk of identifiability has been managed.
Sources & References
- ARDC. Publishing Sensitive Data
- HKUST. Acceptable Practices for Handling High Risk Data
- HKUST. HKUST Data Classification Guidelines
- HKUST. Protect My Data
- HKUST. Risk Classification Examples of Common IT Resources
- HKUST Research Bridge. Nature Research Academies: Sharing Sensitive Data (Nov 2020)
- OpenAIRE. How to deal with sensitive data
– By Jennifer Gu, Library
Hits: 296
Go Back to page Top
- Category:
- Research Data Management Tips
Tags: data encryption, data security, data sharing, FAIR principles, research data management
published March 31, 2023


